I’ve been trying to enable the passive port range on an IIS6 FTP server. I did everything. I enabled direct metabase edit, set the range using ADSUTIL and then added the ports to the firewall.
It turns out that if you set the firewall to allow “FTP”, the passive port range will be ignored and the default passive port range will be used. To solve it, you’ll need to manually add port 21 and the ports defined in the passive port range… Strange but true.
If you’ve been following along in my blog, I’ve recently had to reinstall Windows onto my server as it turned out that I couldn’t resize (grow) the RAID array.
Things are almost completely back to normal now. One problem I had was getting FTP under IIS 6.0 to work properly through my firewall.
Overview of the FTP protocol
In terms of Internet protocol (TCP), FTP is a strange one. It uses port 21 as a control port and then other (sometimes) random ports for down/up loading. This effectively means that when you request to download a file, your FTP client connects to the server on port 21, sending through your username, password and changing to the correct directory.
Under old-school (Active, or Non-Passive) FTP, as soon as a file is requested for download (Using the command RETR), the server will tell the client to get ready to receive the data on a particular port. The main thing to note being that the Server Connects to the Client to send/receive files. This creates numerous problems for users behind firewalls.
I now introduce Passive FTP. The main difference is that the Client Connects to the Server to send/receive files. When Passive FTP is used, the client sends the server the command PASV which commands the server to supply a port number, but then wait for the client to connect to it.
Why this is a problem
Passive mode becomes a problem when the server is behind a firewall. When this is the case, the range of ports to be used needs to be known in advance and in almost all cases, allowed to pass through the firewall to the server.
IIS 6.0 by default uses the port range of 5000-65535. To open all these ports on a firewall would be a massive security risk. To limit this risk, you can set a smaller range of ports to be used.
To set the range of ports to be used in IIS, it’s a fairly trivial task…
1. Open IIS manager, right click the root (local computer) and select properties.
2. Select “Enable Direct Metabase Edit” (see image below)
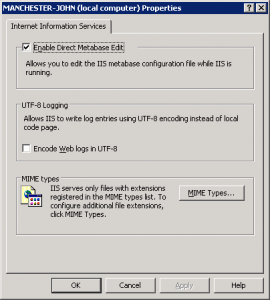
3. OK all the way out of IIS.
Enabling direct metabase edit means that you can use command line tools to edit IIS settings.
Once this is done, the following, if run from a command line, will enable the port range 6000-6100
cscript C:\Inetpub\AdminScripts\adsutil.vbs set /MSFTPSVC/PassivePortRange "6000-6100"
And the following, if run from a command line, will enable the range 6000-6100 through the firewall
FOR /L %%I IN (6000,1,6100) DO NETSH FIREWALL add PORTOPENING TCP %%I FTPPort%%I
Now, simply reset IIS and you “should” be on your way
IISRESET
Unfortunately, this isn’t always the case….
I was finding that while the windows firewall was disabled, the selected port range would work, but as soon as I enabled the firewall, the range went back to the default. The solution to this bug is surprisingly simple.
Open the windows firewall and click the advanced tab:
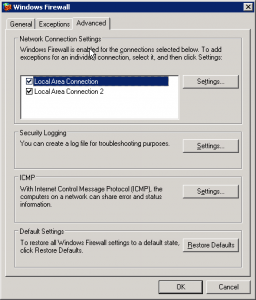
Select your network connect and click [settings]. In this list, if you have “FTP Server” selected, deselect it and click OK. Do this for all network interfaces you have.
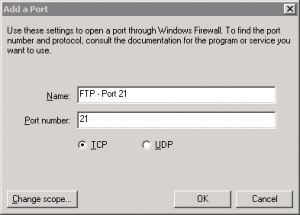
Now, back in the main firewall screen, select the Exceptions tab, and click the Add Port button. Give your new exception a meaningful name, enter port 21 and select TCP.
Strangely this will work with your Passive Port Range while the program exception on a Network connection basis will not. I spent hours trying to work this out so hopefully someone else will find it useful.

Hi chap,
I’m new to Windows Server and was bashing my head trying to get Passive Mode working after entering all the ports into the firewall.
Thanks for the top bit of info!
Simon
Amazing, I would have never tried that. Thank you, it fix my passive FTP connection issues!
“It turns out that if you set the firewall to allow “FTP”, the passive port range will be ignored and the default passive port range will be used.”
I cant believe it!! I have been fighting a whole week with windows firewall, because of this “strange” behavior.
Thanks for the solution
Thank you very much for this tip!!!
I was becoming crazy with this shit!
Regards.
%%I should be %I
FOR /L %I IN (6000,1,6100) DO NETSH FIREWALL add PORTOPENING TCP %I FTPPort%I